Digital transformation propositions have been successfully applied in various fields for a few years now, as key enablers came to fruition. As a result, new businesses are being launched and existing businesses are being revitalised after a digital transformation. It is likely that one or more of these propositions can also generate significant added value for you.
From enablers to propositions
In this article we will provide some examples of propositions based on the enabling hardware, software, science or infra. Technological progress and the availability of affordable infrastructure capacity, to store data and process calculations, are often the reason why some of the enablers came to fruition now, after decades of research.
It is not our intention to provide a full repository and to elaborate on all use cases here. The scope of this article is summarized in the image underneath. The image is based on the digital transformation presentation scheme introduced by Roland Berger. Please mind that propositions are often linked to more than one enabler and enablers can reside in different areas of digital transformation.
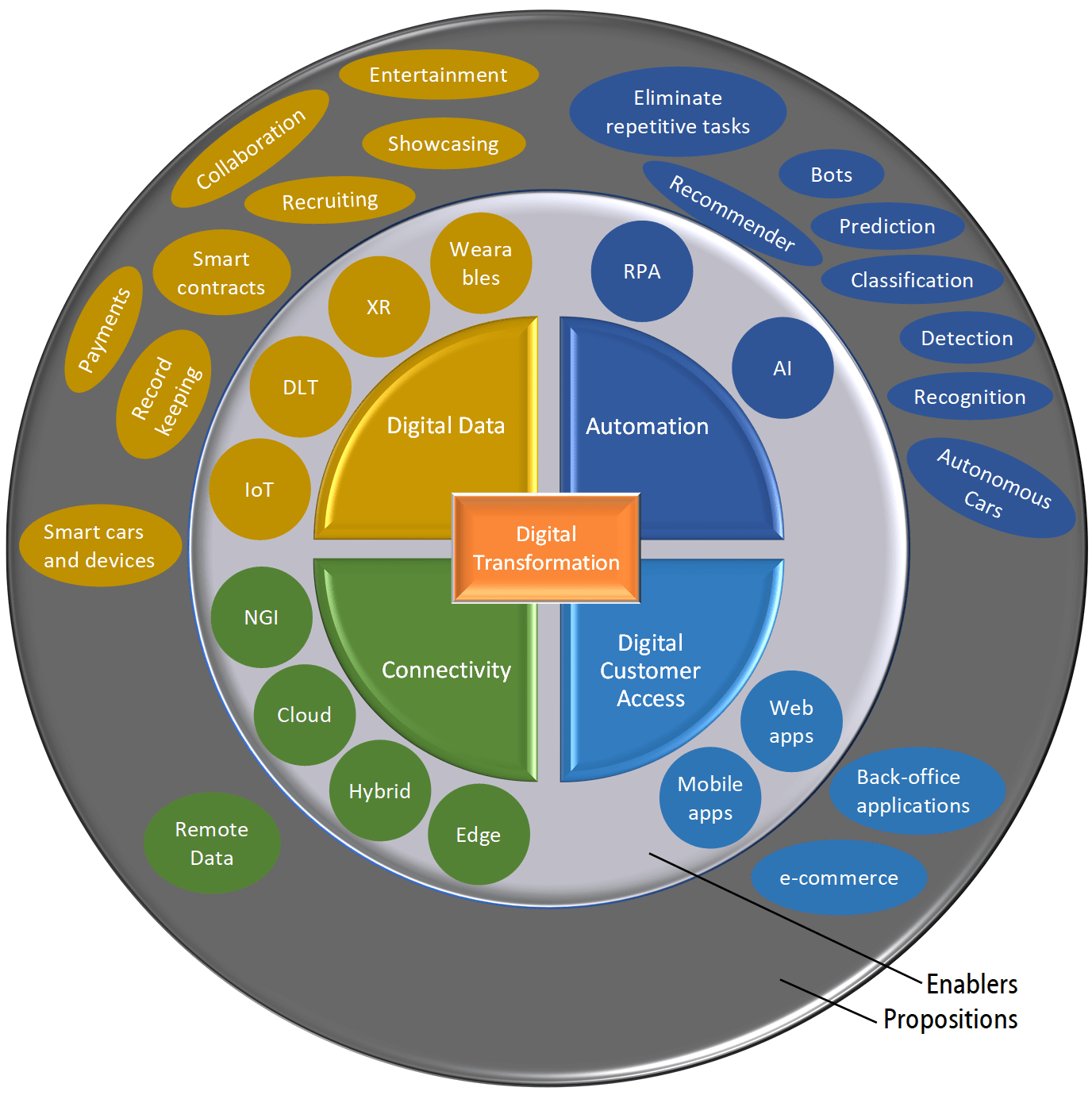
- technology where software robots (Bots) mimic human actions to complete tasks normally done by people
- software designed to eliminate manual and repetitive tasks and does not correlate to human intelligence
- typically applied in situations where documents and information from various sources needs to be combined and tasks need to be performed over multiple applications and user interfaces
- allows to reduce repetitive and monotonous tasks, which can be done faster and at reduced costs automatically
- allows for end-to-end automation and improved customer experience
Examples can be found in KYC processes (Know Your Customer), Account Opening Processes (AOP) and fraud alert handling.
Artificial Intelligence (AI) is about computer systems able to perform tasks normally requiring human intelligence. It covers a broad family of technologies, trying to capture and mimic human intelligence.
In classic programming, data and rules are used to obtain answers. AI is about combining data and answers, to generate the rules behind them, in order to predict new answers when new data is provided.
Although AI concepts date back from the 1950s, the technology has entered our daily lives and economies only recently, e.g. proposed text in Google search or spam filter on mailboxes. The reason why AI is emerging now, after decades of research, is due to:
- Technological progress and the availability of affordable infrastructure capacity to store data (e.g. Cloud) and process calculations (e.g. algorithms)
- Progress being made regarding big data and IoT (Internet of Things); since AI is often involved, it is benefitting
- Human parity achieved since 2016 in a number of fields; equal or better than human results
However, disruption or general revolution by AI is not to be expected in the coming years.
In following areas, AI can currently be applied successfully:
- Image classification
- Email/document classification
- Chat/Voice bot
- Sentiment Analysis
- Object/Person detection
- Information extraction
AI can be further categorized into subcategories of which the main are:
Machine Learning (ML)
- a subset of AI and driven by data
- the scientific study of algorithms and statistical models that computer systems use to perform a specific task without using explicit instructions, relying on patterns and inference instead
Examples of ML are the recommender functionalities offered by e.g. Netflix, Spotify, YouTube, Amazon and eBay.
Deep Learning (DL)
- a further subset of ML
- more powerful, layered and based on artificial neural networks
Examples of DL can be found in voice and image recognition.
ML can be further divided into 3 main types: Supervised Learning (SL), Unsupervised Learning (UL) and Reinforcement Learning (RL).
Supervised Learning (SL)
Learning from labelled training data, e.g. pictures of dogs and of cats. Computer will predict the classification of new (unlabelled) data. Next time you show a dog, the SL algorithm can tell you it is a dog. Task Driven.
SL is used for:
- Classification: predicting to which class an input belongs, e.g. a cat
- Regression: predicting a value (quantity related) based on a number of inputs, e.g. tomorrow it’s a rainy day for 40%
Unsupervised Learning (UL)
Learning from unlabelled training data. Computer is only told there are e.g. two groups. Computer has to find out the hidden structure and will predict the cluster to which new data delivered belongs.
UL is used for:
- Clustering: to find similarities in datasets and to group similar data, e.g. recommender systems predicting the preference of a user
- Anomaly detection: to detect something that doesn’t really belong to the group(s), e.g. spam filter, fraudulent invoices, fraudulent transactions…
Reinforcement Learning (RL)
Computer learns based upon rewards (reward system) and punishments (learns from mistakes). The algorithm learns a decision process or series of actions, e.g. learns to play a game (points versus dying player).
Next to the above data driven AI techniques, there are knowledge driven techniques like Reasoning, used for e.g. search, optimization, planning and scheduling and knowledge representation.
AI Implementation
An implementation requires often combinations. For one project often different techniques are combined, or AI is used in combination with other sciences:
- Supervised deep learning combined with Linguistics (Natural Language Recognition) to structure data (voice recognition) and perform sentiment classification
- Supervised deep learning combined with Computer Vision to structure data (image recognition) and perform accounting or to classify medical x-ray images
- Reinforcement learning combined with Robotics to train robots
An example of an AI project diagram can be found here.
Mobile and web apps form and support front-and back-offices. Two major innovations account for their success: low/no-code development platforms and Application Programming Interfaces (APIs).
Low/no-code development platforms
- user-friendly development environments that allow to drag and drop application components in a graphical user interface (GUI)
- allow for easy connectivity/interfacing via third-party APIs
- reduce development time for professional developers
- allow for non-professional developers to build too
- narrow the gap between business operations and IT development: the configuration or code required is often as writable and readable as functional business specifications
- enable to be more agile
In back-offices, often Excel or Access based tools have been developed in the past. The conversion, of such tools into low-code or no-code micro apps (e.g. Mendix), allows for more robustness, more security and improved maintainability. Such conversion perfectly fits in a digital transformation as it allows to migrate to cloud computing and to include propositions like e.g. artificial intelligence.
Application Programming Interfaces (APIs)
An API platform is an organization, which brings together two or more distinct, but interdependent groups, through a programmatically consumable service or an Application Programming Interface (API), creating a foundation for automated interactions between them.
The open landscapes, introduced because of business or regulatory reasons (e.g. open banking (PSD2)), are benefitting from Application Programming Interfaces (APIs), allowing for easy connectivity.
New ways of computing were key enablers for Digital Transformation:
- Cloud computing: on-demand availability of computer system resources, especially data storage and computing power, without direct active management by the user
- Hybrid computing: combines data stored on-premise with a cloud
- Edge computing: used when devices need to be able to work independently from a cloud
Hybrid computing can be recommended for regulatory purposes (e.g. data cannot leave the area) or in case of bad connectivity (e.g. a ship in the sea).
Edge computing is used if additional contextual data is captured from local sensors. In that case a cloud can e.g. push new Machine Learning (ML) models to autonomous devices like e.g. autonomous cars, smart drones and smart surveillance cameras. During their operation, the devices can process the ML models independently with local data.
The migration to new ways of computing generally involves hardware decommissioning, data migration, service provider selection and contracting, new service level agreements and new support procedures and software.
IoT (Internet of Things) is a network of uniquely identifiable “things”, communicating with each other without human interaction/intervention.
Examples are smart cars and smart devices (e.g. thermostat, kitchen appliances).
IoT is often combined with other technologies like AI, blockchain or Next Generation Internet (NGI).
Distributed Ledger Technology (DLT)
A distributed ledger is a consensus of replicated, shared, and synchronized digital data geographically spread across multiple sites, countries, or institutions. It is simply a replicated, shared and synchronized database with no central administrator or centralized data storage.
A peer-to-peer network is required as well as consensus algorithms, to ensure replication across nodes is undertaken. The distributed ledger database is spread across several nodes (devices) on a peer-to-peer network, where each replicates and saves an identical copy of the ledger and updates itself independently. Security is accomplished through cryptographic keys and signatures.
The distributed ledger records the transactions, such as the exchange of assets or data, among the participants in the network.
It allows transactions to have public witnesses.
Blockchain
One type of distributed ledger is the blockchain system, which can be either public or private. The name blockchain refers to the “blocks” that get added to the chain of transaction records. Each block is secured with a hash.
Blockchain allows digital data to be distributed, while enabling multiple parties (e.g. individuals, companies, financial institutions, public institutions) to work on a shared set of data.
Blockchain has been researched and/or used for:
- Government/Banking: to settle a mortgage (notary, bank, financial advisor)
- Banking: to support Know Your Customer and Anti Money Laundering obligations
- Trade Finance: to accommodate letter of credits
- Payments: to allow for faster/cheaper (international) payments or to enable for cryptocurrencies
- Insurance: to accommodate claims handling
- Charity: to support collection of funds in full transparency
- Supply Chain Management: to track goods
- Fixed Assets Protection: to track assets (e.g. in combination with IoT)
- Healthcare: to keep medical records
- Real estate: to support asset transactions
- Energy: to support energy supply, reporting and billing
- …
Extended Reality (XR) refers to all real-and-virtual combined environments and human-machine interactions generated by computer technology and wearables.
XR can be further categorized into Virtual Reality (VR), Augmented Reality (AR) and a mixture of both:
- Virtual Reality (VR): a simulated experience that can be similar to or completely different from the real world
- Augmented Reality (AR): an interactive experience of a real-world environment where the objects that reside in the real world are enhanced by computer-generated perceptual information (visual objects, audio or other) (e.g. The Pokémon game)
VR and AR can be used for:
- Entertainment (e.g. video games)
- Educational purposes and training (e.g. emergency services)
- Storytelling
- Prototyping (e.g. architecture)
- Showcases (e.g. home furnishing)
- Collaboration (virtual in person speeches)
- Recruiting (virtual in person recruiting)
Explore thoughtfully what digital transformation can bring to you
It is important to gain awareness and understanding of the propositions and enablers and their potential impact for you or the business ecosystem(s) you are part of, as they can improve competitivity or offer market opportunities.
Make sure to elaborate on elements like trust, ethics, compliance and security while calculating the ROI of the application in your context.
It is important to have the right capabilities and competences on board to start your exploration journey.
Make sure to tune your organization for business agility, to adopt the digital transformation more easily. Often business agility requires first steps in the field of digital transformation.
How can we help you?
We are happy to discuss what we can do for you.
- Do you want a sounding board to discuss digital transformation propositions or enablers?
- Do you want to assess the opportunities, impact or the business case for your business?
- Are you planning to take the next steps in your digital transformation?
- Do you have a program/project to be initiated, managed or delivered?
Let us know.





